In this tutorial, we will learn What is Web Vulnerability? Also, explain four web vulnerabilities. At its core, a Web Vulnerability refers to a weakness or flaw present in a website or web application that cybercriminals can exploit to compromise its integrity, data confidentiality, and overall security. What is a Web Vulnerability? Web vulnerabilities represent loopholes or misconfigurations in the code of a website or online application, providing an entry point for hackers to acquire control. Hackers use automated tools to keep searching to detect such weaknesses. Then, they take…
Read MoreCategory: Security
Explain the Concept and Need of Cyber Defense
Key to Cyber Defense is the ability to detect and mitigate attacks. Organizations should establish transparent internal policies, ensuring employees consistently follow cybersecurity best practices, along with preventative and mitigation measures. A single security breach could lead to significant consequences for an organization. The assurance of safety and data security relies on the effective implementation of proper detection and counter techniques against Cyber threats.
Read MoreWrite and Explain any Two Cyber Attacks, with One Example Each.
In this tutorial, we are going to answer the question “Write and Explain any Two Cyber Attacks, with One Example Each“. What is Cyber Attack? A cyber attack is a deliberate, malicious act aimed at compromising the integrity, confidentiality, or availability of digital systems, networks, or data. It involves unauthorized access, manipulation, or disruption of computer systems by cyber criminals with the intent to steal sensitive information, cause harm, or disrupt normal operations. Cyber attacks come in various forms, including phishing, malware infections, denial-of-service attacks, and more. These incidents pose…
Read MoreWhat is Cyber Security?
Cyber Security refers to the technologies, procedures, and protocols designed to safeguard Computers, Servers, Mobile Devices, Electronic Systems, IoT Devices, Networks, and data from unauthorized access, vulnerabilities, attacks or damage carried out by cybercriminals via the Internet.
Read MoreHow SSL make HTTP Secure
In this article, we will learn How SSL make HTTP Secure. SSL stands for Secure Socket Layer. SSL has been succeeded by TLS (Transport Layer Security). Even though TLS has replaced SSL, people still commonly use the term “SSL” to talk about secure communication on the web.
Read MoreTypes of Hackers
In this article, we will learn about different types of Hackers. While talking about hackers, most people think of them as cyber-criminal. Hackers are not Cyber-criminals. The media is responsible for portraying the term Hacker negatively.
Read MoreWhat is Computer Virus?
In this article, we will learn, What is Computer Virus? Symptoms of a Computer Virus? How Computer Virus Work? Types of Computer Viruses etc. We are living in a world of Viruses. Hence it is very important to have at least basic knowledge of Viruses.
Read MoreHow to Create a Group in Symantec Endpoint Protection Manager
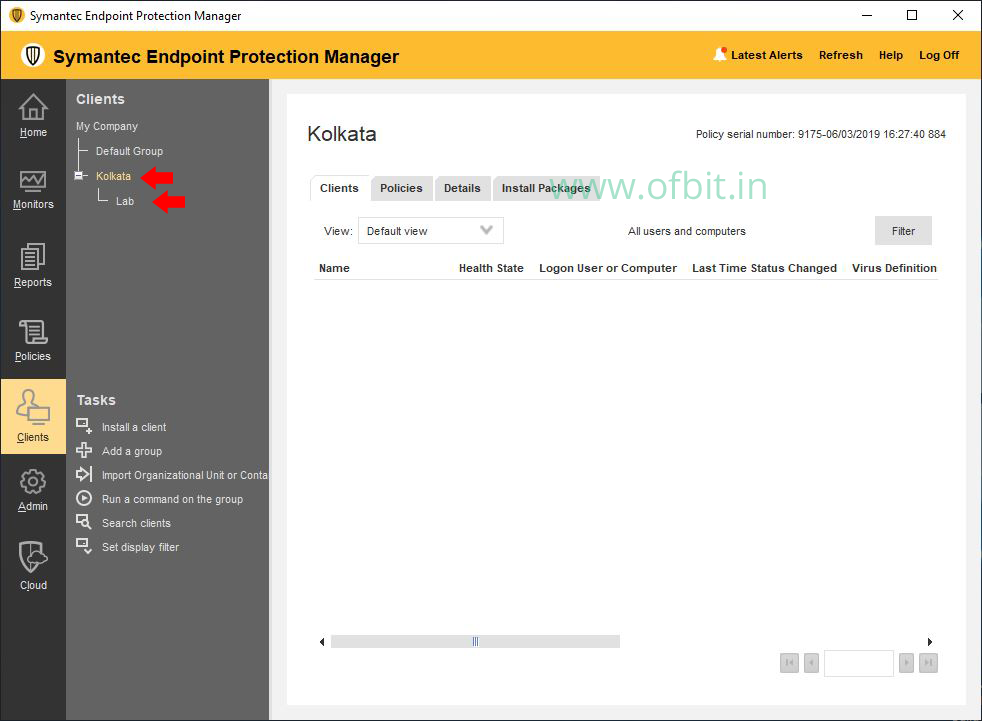
In this article, you will learn How to Create a Group in Symantec Endpoint Protection Manager. Creating a group is like a container for the endpoints that are run Symantec Endpoint Protection client software.
Read MoreHow to Install Symantec Endpoint Protection in Linux (with Screenshot)
In this article, we will learn How to Install Symantec Endpoint Protection in Linux. We are going to perform this SEP client installation on CentOS. Although we can use these steps on RHEL and Fedora as well. We will install Symantec Endpoint Protection 14.3 in CentOS 8. CentOS is a Linux distribution that provides a free, community-supported computing platform functionally compatible with its upstream source, Red Hat Enterprise Linux. Pre-requisite check before installing SEP in Linux Before the installation, it is recommended to check the Supported Linux kernels for Endpoint…
Read MoreCEH v11 Launched – What is New?
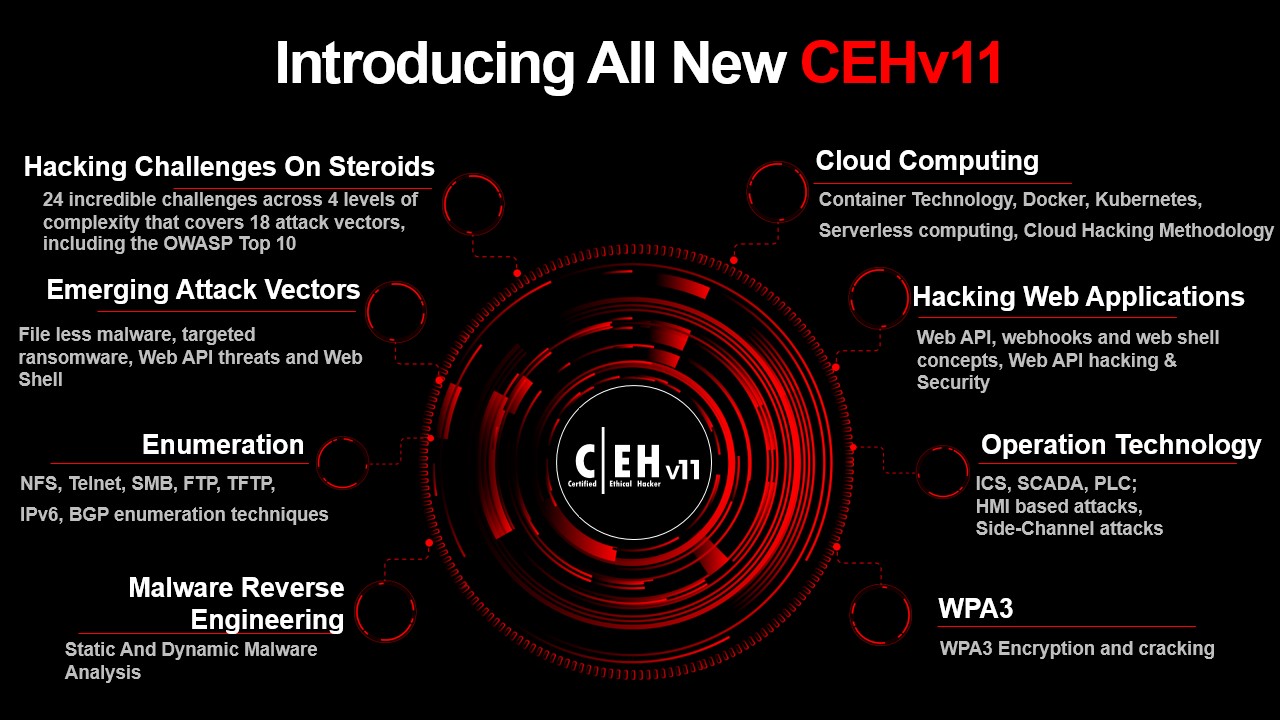
CEH V11, The ultimate Ethical Hacking Certification. EC-Council introducing a new version of the CEH: Certified Ethical Hacker Version 11. This Version covers the latest commercial-grade hacking tools, techniques, and methodologies used by hackers and information security professionals to lawfully hack an organization.
Read More